- IAM (Identity Access Management) allows you to manage users, groups, permissions (level of access) to the AWS console
- S3 (Simple Storage Service) provides a files storage service
IAM has a global view, not like EC2 or S3 has a Region
IAM Features
IAM offers the following features:
- Centralized control of your AWS account
- Shared Access to your AWS account
- Granular Permissions
- Identity Federation (Active Directory, Github …)
- Multi-Factor Authentication
- Provide temporary access for users/devices and services where necessary
- Allows you to set up your password rotation policy
- integrates with many different AWS services
- Support PCI DSS Compliance
Terminology of IAM
Next, let’s get familiar with some terminology of IAM:
- Users, Groups, Roles (I think these are naive so I just list them here)
- Policies, this is a JSON formatted file, call Policy Document
IAM - Advanced
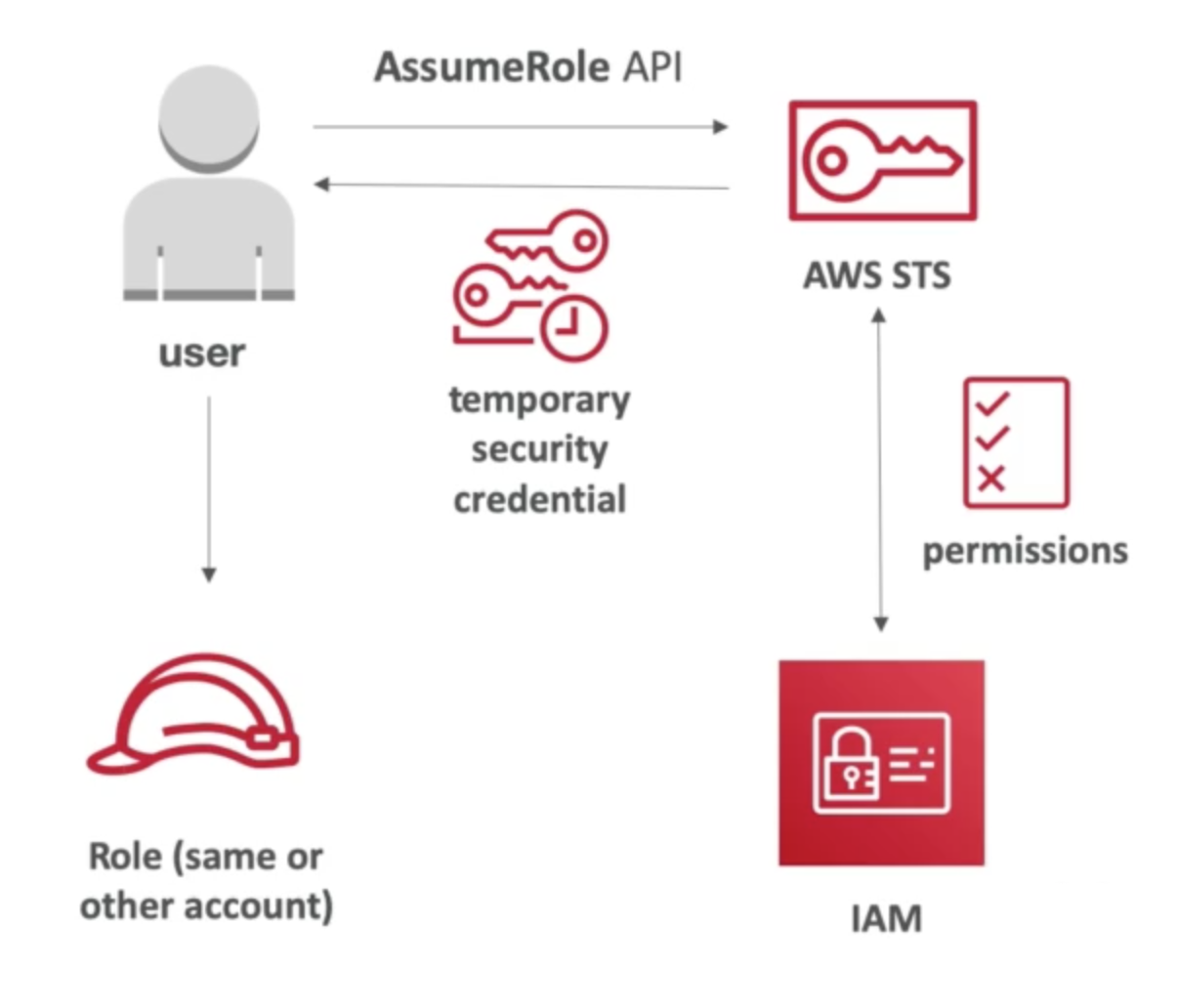
AWS STS - Security Token Service
- Allows granting limited and temporary access to AWS resources
- Token is valid for up to one hour (must be refreshed)
AssumeRoleAssumeRoleWithSAMLAssumeRoleWithWebIdentityGetSessionToken
Using STS to Assume a Role
- Define an IAM Role within your account or cross-account
- Define which principals can access this IAM Role
- Use AWS STS to retrieve credentials and impersonate the IAM Role you have access to (
AssumeRoleAPI) - Temporary credentials can be valid between 15 minutes to 1 hour
Directory Services
- AWS Managed Microsoft AD
- Create your AD in AWS, manage users locally, supports MFA
- Establish trust connections with your on-premise AD
- AD Connector
- Directory Gateway (proxy) to redirect to on-premise AD
- Users are managed on the on-premise AD
- Simple AD
- AD-compatible managed directory on AWS
- Cannot be joined with on-premise AD
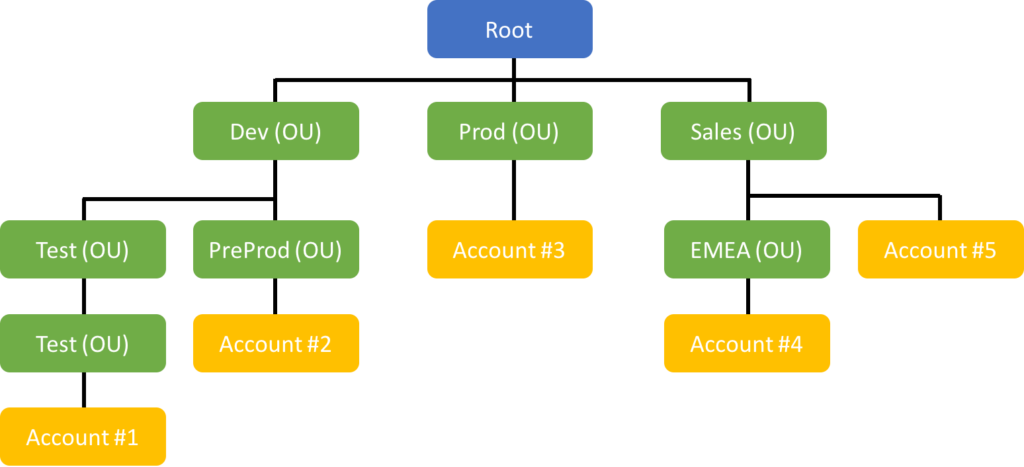
AWS Organizations
- Global service
- Allows managing multiple AWS accounts
- The main account is the master account (cannot change this)
- Other accounts are member accounts
- Member accounts can only be part of one organization
- Consolidated billing across all accounts - one payment method
- API is available to automate AWS account creation
Organization Units (OU)
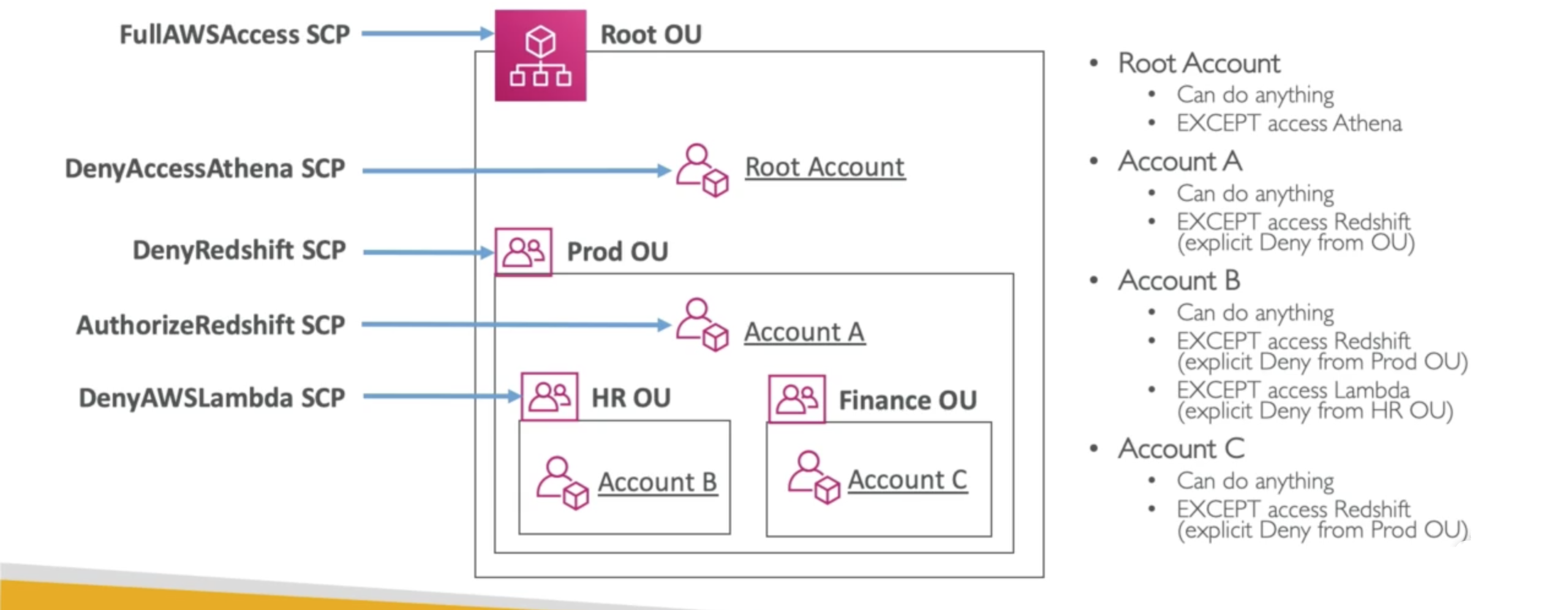
Service Control Policies (SCP)
SCP contains Allowlist or denylist IAM actions and can be applied at the Root, OU, or Account level
- SCP is applied to all the Users and Roles of the Account, including Root
- The SCP does not affect service-linked roles
- service-linked roles enable other AWS services to integrate with AWS Organizations and cannot be restricted by SCPs
- SCP must have an explicit
Allowrule (since it does not allow anything by default)
some use cases:
- Restrict access to certain services (like customer team cannot use EC2, but can use S3)
- Enforce PCI compliance by explicitly disabling services
SCP Hierarchy
AWS Organizations - Moving Accounts
Migrate accounts from Organization A to Organization B
- Remove the member account from Organization A
- Send an invite to Organization B
- Accept the invite from the member account
Migrate master (or primary) account of Organization A to Organization B
- Remove the member account from Organization A
- Delete Organization A
- Repeat the process above to invite the old master account to Organization B
Advanced IAM
IAM Roles vs Resource-Based Policies
Attach a policy to a resource versus attaching of a using a role as a proxy (STS)
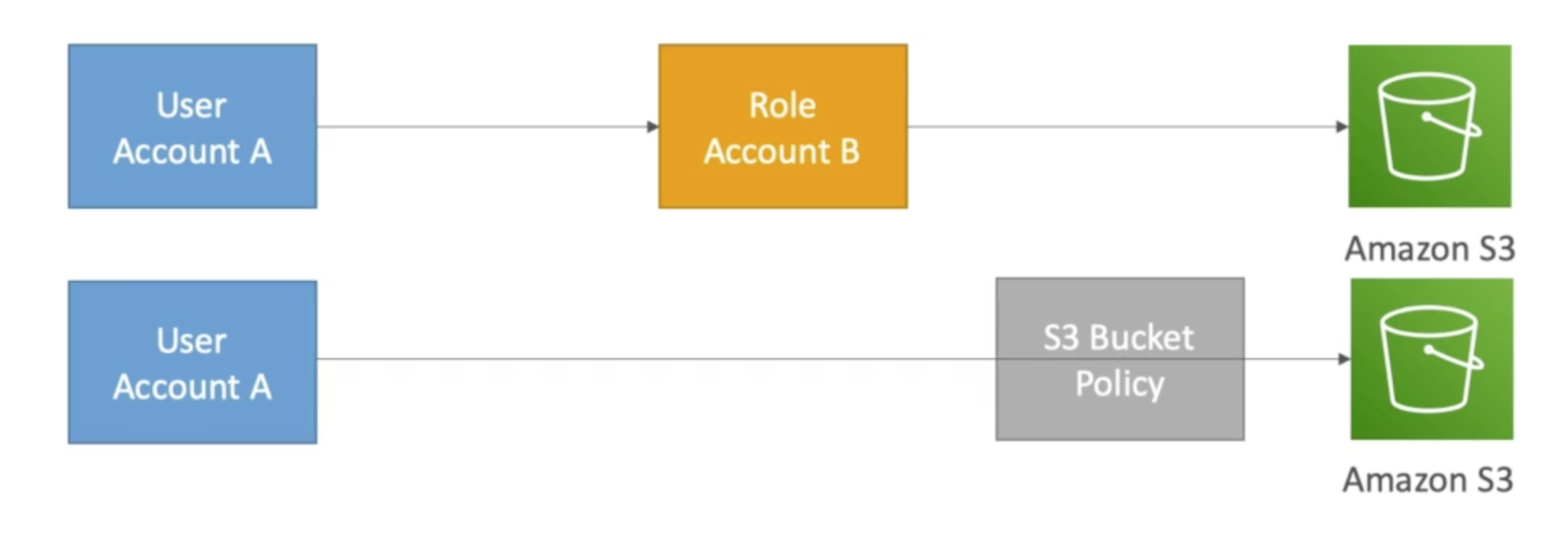
- When you assume a role (user, application, or service), you give up your original permissions and take the permissions assigned to the role
- When using a resource-based policy, the principal does not have to give up his permissions
IAM - Policy Evaluation Logic
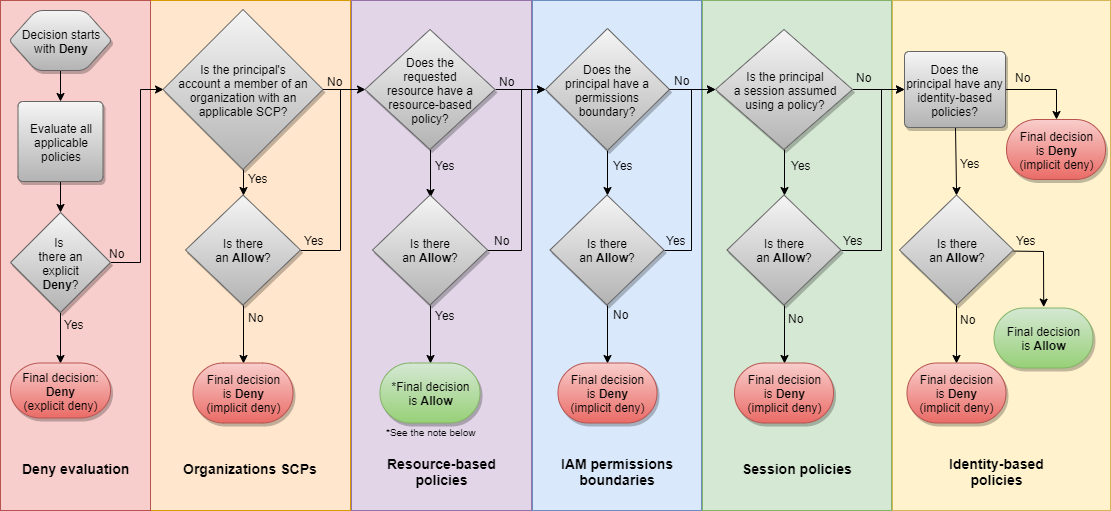
As soon as there is an explicit deny, the result will be denied
1
2
3
4
5
6
7
8
9
10
11
12
13
14
"Statement": [
{
"Action": "sqs:*",
"Effect": "Deny",
"Resource": "*"
},
{
"Action": [
"sqs:DeleteQueue"
],
"Effect": "Allow",
"Resource": "*"
}
]
- sqs:CreateQueue -> NO
- sqs:DeleteQueue -> NO, since there is an explicit DENY
- ec2:DescribeInstances -> NO, there is no explicit ALLOW
AWS Resource Access Manager (RAM)
- Share AWS resources that you own with other AWS accounts
- Share with any account or within your Organization
- VPC Subnets, AWS Transit Gateway, Route53 Resolver Rules, License Manager Configurations
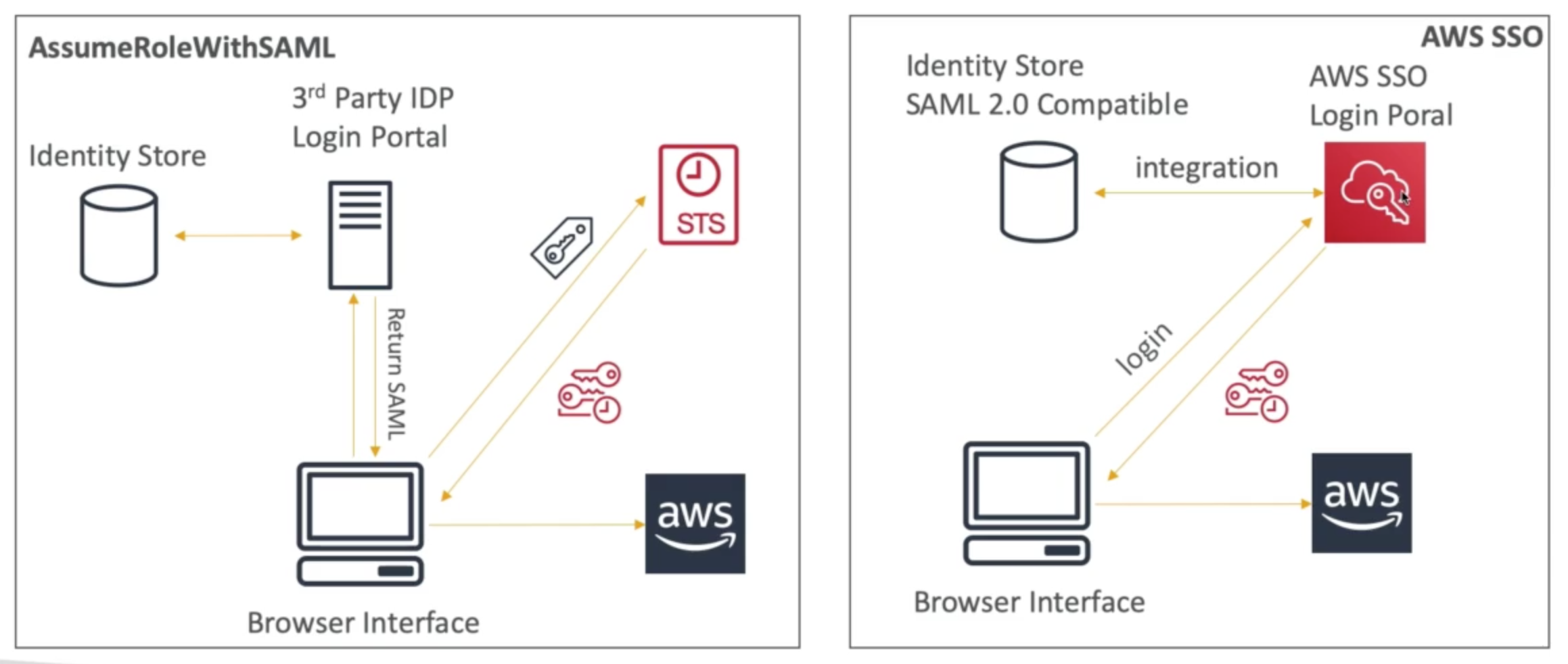
AWS Single Sign-On (SSO)
- Centrally manage Single Sign-On to access multiple accounts and 3rd party business applications
- Integrated with AWS Organizations
- Support SAML 2.0 markup
- Integration with on-premise Active Directory
- Centralized permission management
- Centralized auditing with CloudTrail
SSO vs AssumeRoleWithSAML